Czech Cybersecurity Competition Quals Writeup

Kybersoutěž AKA Czech Cybersecurity Competition is a "CTF" for high school/university students in the Czech Republic. It consists of two rounds and finals. The first round is a survey covering basic CS terms and definitions. The second round, which is covered in the blog post, is more CTF-like. Both take place online. After them, if you qualify, you go to the final, which is an on-site one-day CTF. Individual phase in the morning followed by a team phase in the afternoon. If you do good in the finals, you enter a pool of participants from which you can qualify for the ECSC Czech Team for that year.
Even though it has its problems, Kybersoutěž is what got me in cybersecurity in the first place (when I first participated in 2018), each year packs some interesting challenges (esp. crypto <3) and most importantly it opens doors to a lot of incredible people and places, that can take you to a whole new level. I had the honour to participate in ECSC 2019 in Bucharest and it was amazing, if you are a student anywhere in Europe, but especially in the Czech Republic, go and try to qualify.
Anyway, the finals take place in Pilsen this year. I cannot wait to meet everyone again. So see you there!
Challenges
- Phishing / programování - 4 points
- Captured traffic - 8 points
- Šifra KHM - 6 points
- Večeře hackerů - 5 points
- Klasická šifra - 8 points
- Transpoziční šifra - 7 points
- Bruteforce - 2 points
- PCAP zálohy - 4 points
- Únik lékařských záznamů - 5 points
- Forenzní úloha - 5 points
- Zranitelnost - 5 points
- Red Team - 6 points
- Díra na webu - 6 points
- Reverse Proxy - 8 points
- Triviální zranitelnost - 2 points
- URL transformace - 2 points
- UUENCODE - 3 points
- ROT8000 - 4 points
- IoT systém - 4 points
- Statická síťová analýza - 4 points
- ADS - Capture the Flag - 5 points
- Frekvenční analýza - 5 points
- Something Weird - 5 points
- Vernamova šifra - 7 points
- Analýza alertu - 6 points
DISCLAIMER: These are the solutions that managed to get me 121/126 points, so there are definitely some mistakes, but I don’t know where they are, most of the answers should be correct though. There are also a few NOTEs, that came out of the discussion with other participants after the competition.
Phishing / programování
We are tasked to send an email with our email address in Subject to hack@kybercentrum.cz in such a way that it would appear to be sent from info@hacking.cz. If the email is received successfully and isn’t marked as SPAM, we’ll receive a reply to our email address containing the flag.
For certain reasons this will be the only challenge for which I will not disclose the detailed solution here. However this is a well-known challenge and quite a lot of solutions that may work can be found on the internet. If you insist on finding out my solution, you can try contacting me and I might tell you.
If you did everything right, the email with the flag arrived within 30 minutes (at least for me):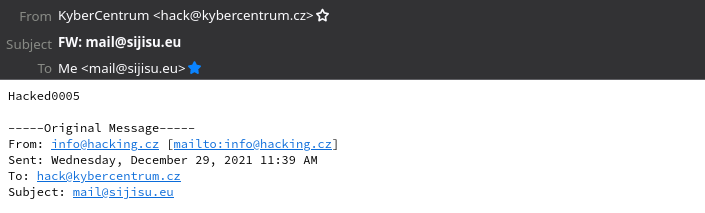
Flag: Hacked0005
Captured traffic
We are presented with a very short PCAP file and we are supposed to find the CVE of the vulnerability that was exploited against the server 192.168.255.2.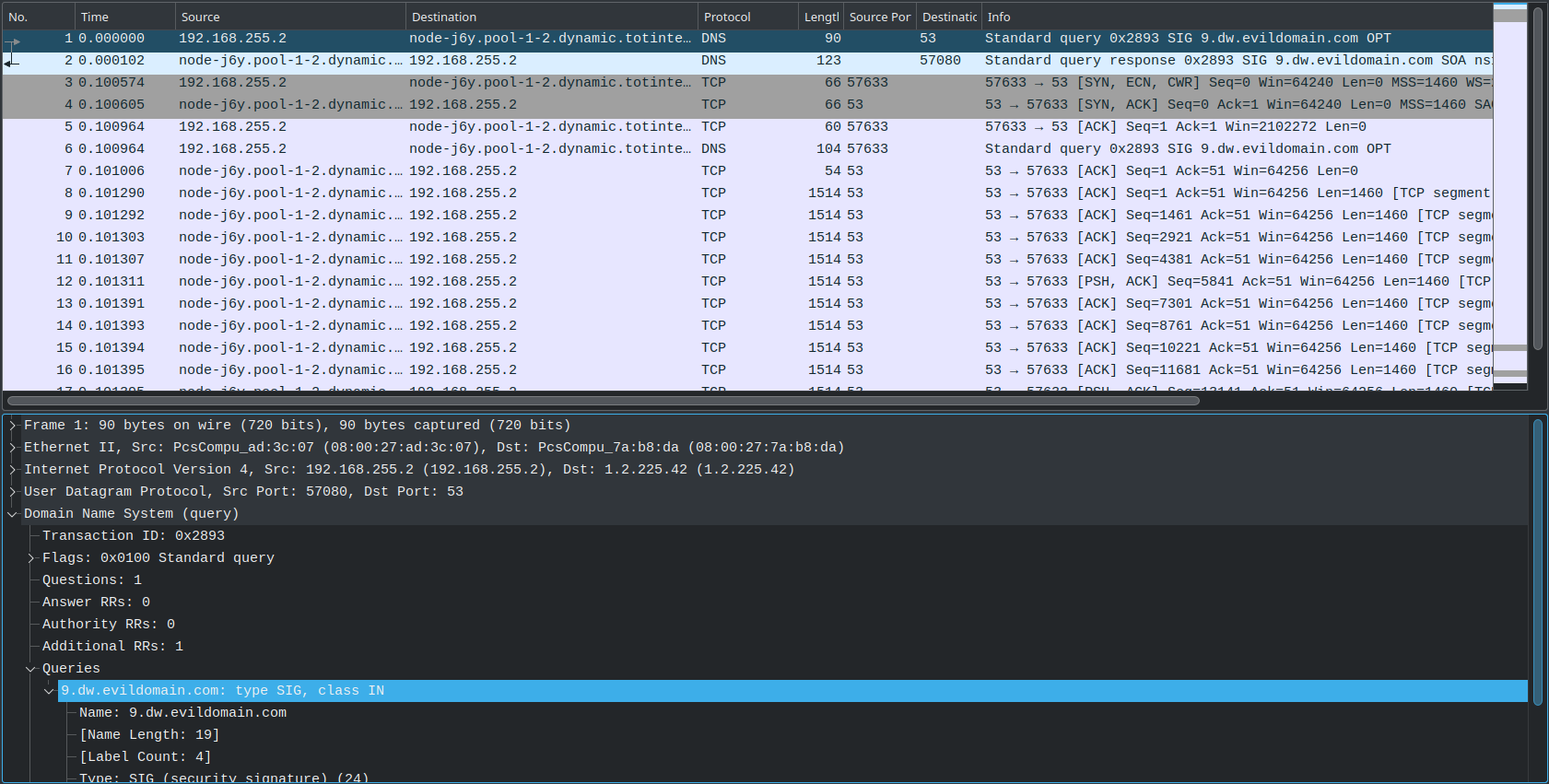
First, we notice that the server makes a DNS request to an unknown address for 9.dw.evildomain.com querying record of type SIG, after that it makes a veeery suspicious TCP connection to the same address. After performing some Googlefu (AKA googling “dns vulnerability sig”), we find a vulnerability called SigRed and identify that its description matches the attack in the PCAP.
Flag: CVE-2020-1350
Šifra KHM
We are supposed to decode the message attached in the description. As a proof, we should provide the last two words of the poem:
The name of the challenge clearly hints to the name of a famous Czech author Karel Hynek Mácha. He is, among many other things, known for keeping an encrypted diary that was only recently fully decrypted. After a bit of googling we find an issue of the Crypto-World magazine from 2011. Where, on page 18, a full decryption table can be found:
Using that table we decipher first few words:
ANILABUT.ANILŮNA
EŘOENYKALBO
LÉ
And then find the corresponding poem.
Flag: ONA TOUŽÍ
Večeře hackerů
Let me provide the full description for this one:
Three hackers were dining at a popular restaurant. At the end of dinner, the waiter announced that one of them had settled the bill for everyone. But he refused to reveal which one had paid. The hackers argued among themselves about who had paid, and whether the person in question had paid out of his own money, or whether the owner of the business who wanted to hire them for a penetration test had. Neither of them admitted to making the payment.
Therefore, the hackers decided to find out (while preserving the anonymity of the one who paid) whether the one who paid for the dinner paid with his own money or with the money of the business owner who wanted to hire them.
After a bit of discussion, they came up with the following procedure:
Each person flips an ordinary coin and informs only the neighbor to his right of the result.
Then each person announces aloud whether his toss and the toss of the neighbor to his left landed on the same side.
The hacker who paid for the dinner and paid for it with his own money reports the opposite match result to the others (if both coins landed on the same side, he reports that the coins landed on different sides and vice versa), and if he paid with the business owner’s money, he reports the true result (match/dismatch)
Everyone will obligatorily follow the above procedure.
They then followed this procedure, and they could tell by the number of matches they reported that the business owner who wanted to hire them had paid for them.
First, we were supposed to find out if, given the result, the number of matches was even or odd. All that was needed was to draw the problem on a piece of paper and the answer was clear - the number of matches was odd. And then we had to find the name of this problem in cryptography, which I found after googling queries similar to “three people flip coins and tell their right neighbor what was the result cryptography protocol” that resulted in the Wikipedia page about the Dining cryptographers problem.
Flag 1: Lichý (“odd” in czech)
Flag 2: Dining cryptographers problem
Klasická šifra
We are provided with the following ciphertext:
RLPSM QMRXN OBLVE TAZOP FTSLF GOIOZ TNTPN PATRT ITEPS MNEOG LRYVT ETZST AFYLF GTEZT NPOGO POQMI MREYI OANPA TRTET ZFYDF
YVZTZ YVLGI LDTVB LFHET VTZTN POSLB LALIY EMIMF PMPAT RTBOP GLRYV TNOIM REYIO ZYRYL FGTEZ TNPTV ONEOZ TXLBD LGYAT XATFG
DOETS LFGOE TVTSL PLAVT BLALX MEOSF TQLHS IOZYE TLFGE METZS TAFYB LGLVP GTDMH NIMRE YIOIB DTSHB LBLFG DRYVT BDTSE YVLFG
ETVZT NPOGO POQMZ TXLSI OPLAV LEOSF TQLHF TEORX ONTZY RYLFG EMBDL EYPAM BDLGY ATXAM VLGIL DTVRL ETZIY RTITE BLGLV NOBDT
SEYLF GTEFP AOBYV TRTAM XAOIL AOVZO PLQMS LAHON ZOPNO SEYSI OIMRE YIOZY RYLFG EMSLI LAYOB LETPH SSLAT IOGYV ZTNTP SLFGO
ETIPA TRYGO PLILH UYWHD HNTIF TRXEM ZTXLL FGOGE YLFGE MPGTD TZYEO PBDTP ONTZY ZTXLI MPALH NEHGY ITENV YNYNZ YEMRX LGILD
HPATR TIZTZ YVIEY GDPHO NOHZV LHBDY NEYIL HBLAL XHPET ZFYDF YVHLG ILDHO BOPFG ORYHN ZTEZT NPTVP DLHGY GNOET ZSTAF YIMRE
YIOZY RYLFG TEFGD YSOIT FTVOG OVBDY GLVFT LFILQ LNHZT ZTNTP FGOAT IYROI YRTFI MVYLF GEMNP ATRTO NZTIT EPHHB AETOE ONBTG
FTSLF GOION BHFLQ TVBDT FETLB OREMV GLHNZ TFEOS ET
As a proof we decrypted the text, we should provide the name of the text author.
After some basic frequency analysis, we find out that it is most probably a substitution cipher. For cracking substitution ciphers I use this tool Cipher-solver by Tomas Hanzak. Right now I’m developing my own tool that will work on Linux, so stay tuned, I’ll be releasing soon :)
After decryption it looked like:
COKDY BYCHZ APOMN ELJAK SEDOS TAVAJ EZEKZ KLECE VENKD YZNAT OCIME NEJDE LSIOS TENJE ZKATA KABYV YCNIV ALZKL ECENE JSIRS
IMJEJ IMOTV OREMP OSUNE MEJEZ KADOP OLOVI NYVYS KYKLE CEPAK TOCIM EZAVY CNIVA JICIO STENJ EZKEM AZNAJ EHOPR OTILE HLEST
RANED OSTAN EMEDO KOLME POLOH YNADS EBOUD VAJIN EOSTN YNEJD ELSIP OTOMK TERYU ZVYCN IVAVP REDUP OPOST RCIME PREDN IMOST
NEMJE ZKATA KABYJ EHODV AKOLM ONADS EBOUS ENACH AZEJI CIOST NYPRO NIKLY PROTI LEHLY MOTVO REMCO NEJVI CEVEN POTOM ZAPRE
DNIOS TENSK LAPIM ECELY HLAVO LAMJA KOBYD OLUAZ JAKZA DNIDV AVYCN IVAJI CIOST NYDOV OLIAP ONEKU DDOLE VATIM JEZEK DOSTA
NEVKL ECITA KOVOU FIGUR UZEVS ECHNY JEHOO STATN IOSTN YKTER EJINA KPREK AZEJI JEHOV YKLOU ZNUTI VENZM IZIZJ INYCH OTVOR
UKLEC EVJEJ IMVNI TRKUA ZAUJM OUPRI ZNIVO UPOLO HUKNE JSIRS IMUOT VORUA PAKST ACIUZ JENJE ZKEMK ROUTI TZANE JDELS IVYCN
IVAJI CIOST ENSTR IDAVE SEMAT AMPRI TOMSE OSVOB OZUJE JEZEK STALE VICAV ICESV YMIOS TNYZK LECEA ZJEVE NKUUP LNEAN AZPET
SEDOS TAVAZ PUSOB EMPRE SNEOP ACNYM TOUZJ ESNAD NE
From that we can identify that the author is Jaroslav Foglar.
Flag: FOGLAR
Transpoziční šifra
As the name suggest, this is going to be a transposition cipher and we are supposed to find the plaintext author again.
We are given the following ciphertext:
IDIPOEPDNBLRAEVCCOEOAAPYAEEDOLHAVIJRVLVUAEROELIEAPNYNAELMJNATECCEMULTASAYPVAYAIVEIAPOYIATNAEEKBELATIHTKMNEMLHLDZAVRAHNSZOIPAVAAKTETESDIITOYIBDLHNDDDBBRNRANNJIYP
After using the handy tool on Dcode.fr we find the following plaintext and key:
2,1,4,5,3 VITELIDEMAJITUTRPELIVOSTHLEDATVPISKUDIAMANTYNEBOPERLYVMORIALEABYHLEDALIVLIDECHVZACNEAPODIVNEDARYODPANABOHAABYNEPRISLYNAZMARTOJEANINENAPADNEATOJEVELIKACHYBACAPEK
And we identify that the author is Karel Čapek.
Flag: CAPEK
Bruteforce
We are provided with a password protected zip archive and a information that the password is not long and is fully numeric.
First, we convert the zip password to john hash format using the zip2john utility (BEWARE: different versions of zip2john work with different archives and other with other archives, this is always like alchemy for me, but trying zip2john in Kali, then the one self-compiled from john-jumbopack and then the one shipped in my distro always worked for me). Once we have the hash we can crack it using john --incremental=Digits ./hash.txt, soon we find the password is 8842316 and inside the archive, we find the flag.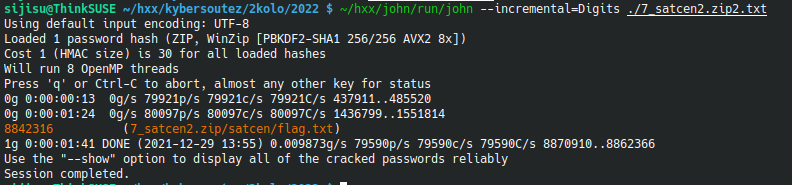
Flag: FLAG{N3b3rUs3Sh0rtPa$$w0rds}
PCAP zálohy
We are given a PCAP from which we are supposed to extract the flag.
In the PCAP we quickly find a FTP session that transfers a file called zaloha.zip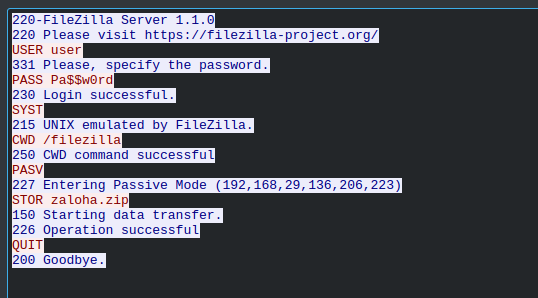
FTP uses a different TCP socket for data streams so we go look for that and quickly identify the correct stream 29 from the .zip file signature letters PK.
We save that stream, open the archive and find a string SYNT{ebg13aravormcrpal} that almost looks like a flag. We decrypt the string with ROT13 and get the flag.
Flag: FLAG{rot13nenibezpecny}
Únik lékařských záznamů
Another day, another PCAP, this time with some “medical data exfiltration” network traffic, we are supposed to find the username of the account that was used for the attack.
After taking a quick look we observe what looks like a bruteforce attack via SMB on an account called rtg and that should be the answer.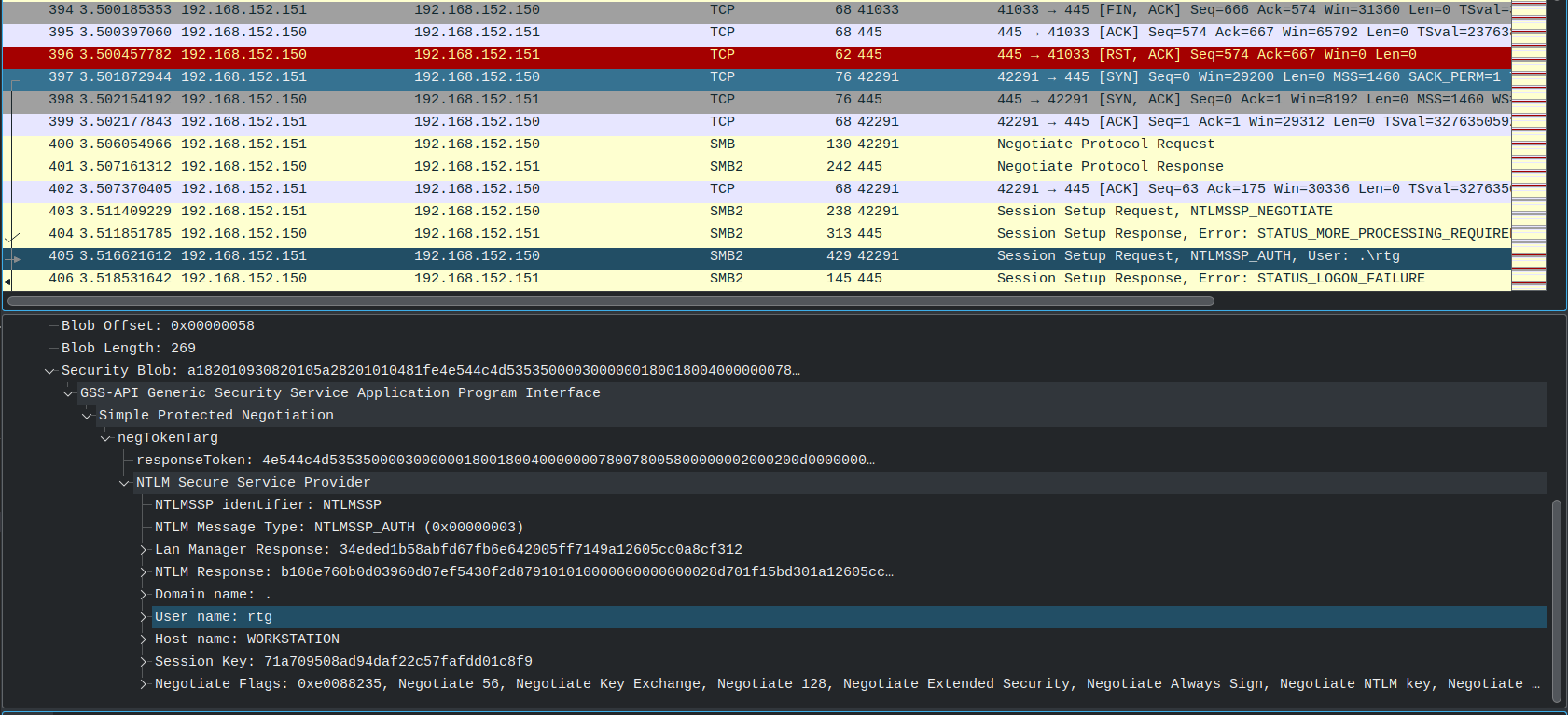
Flag: rtg
Forenzní úloha
We are given a binary called checkme of which is supposed to be a password manager. This is obviously a reverse engineering challenge.
We open it in a disassembler of our choice (it’s .NET bytecode, so our choices are limited), we notice this interesting part: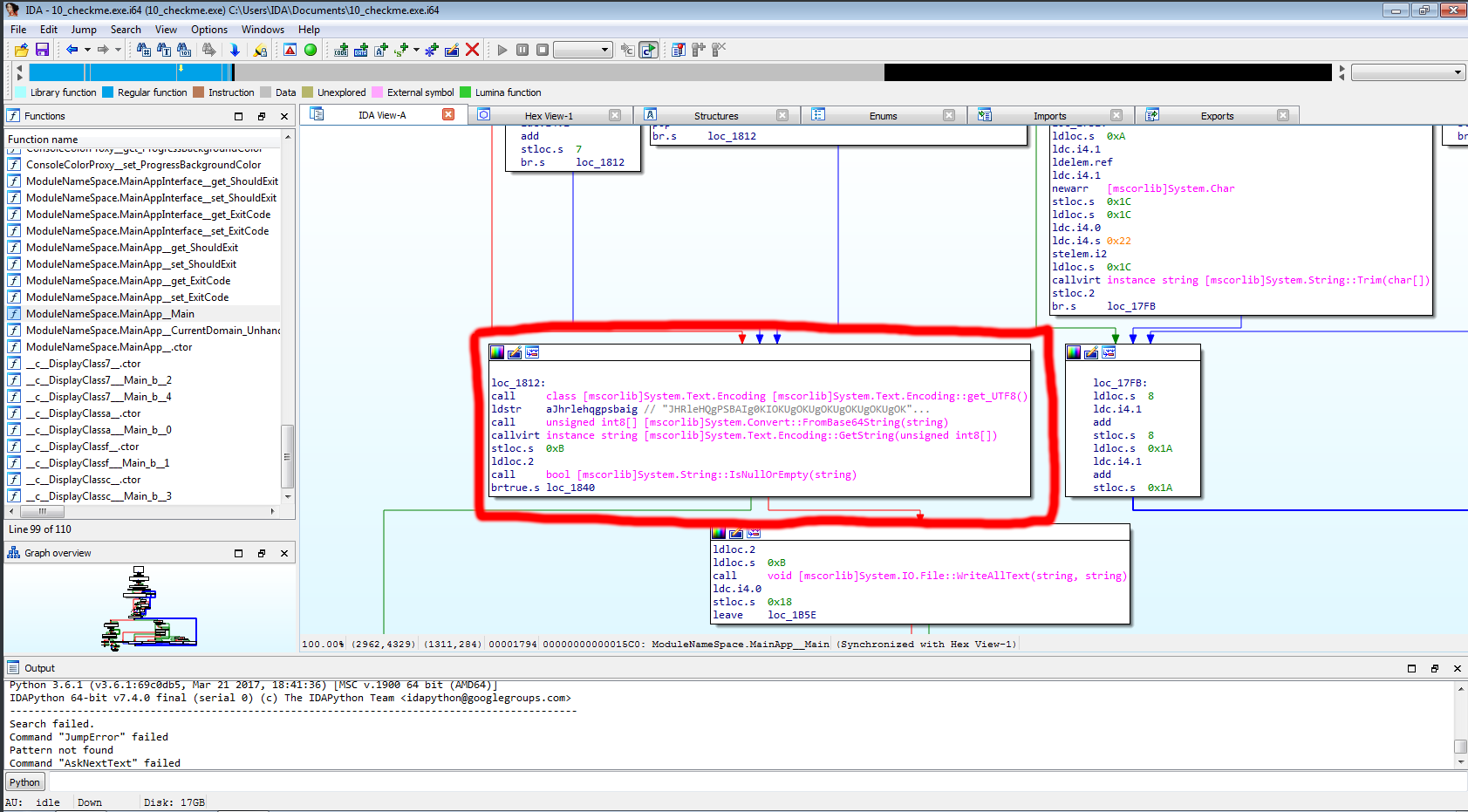
That looks like base64, that is then decoded and what looks like evaled in powershell: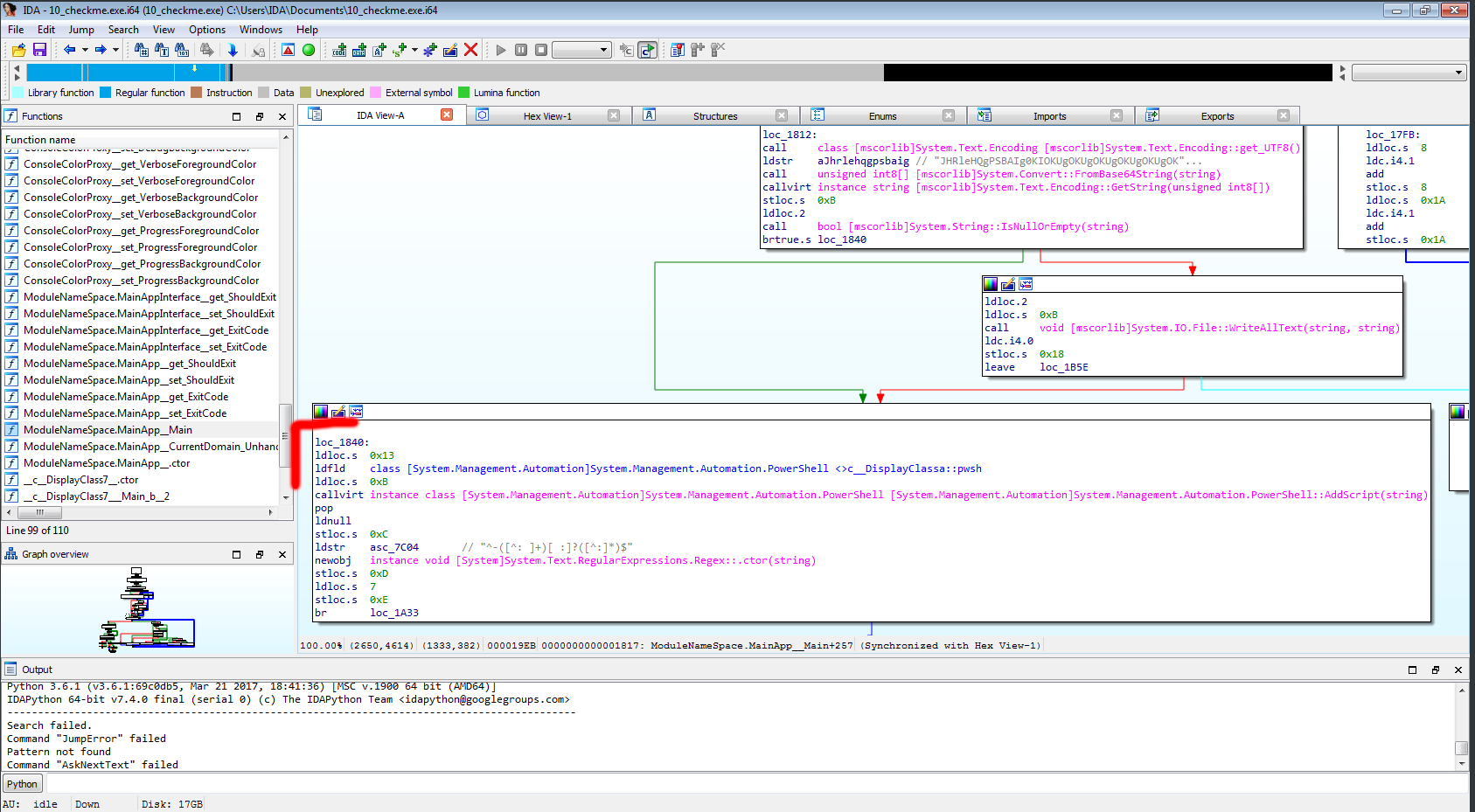
We examine the whole base64 string: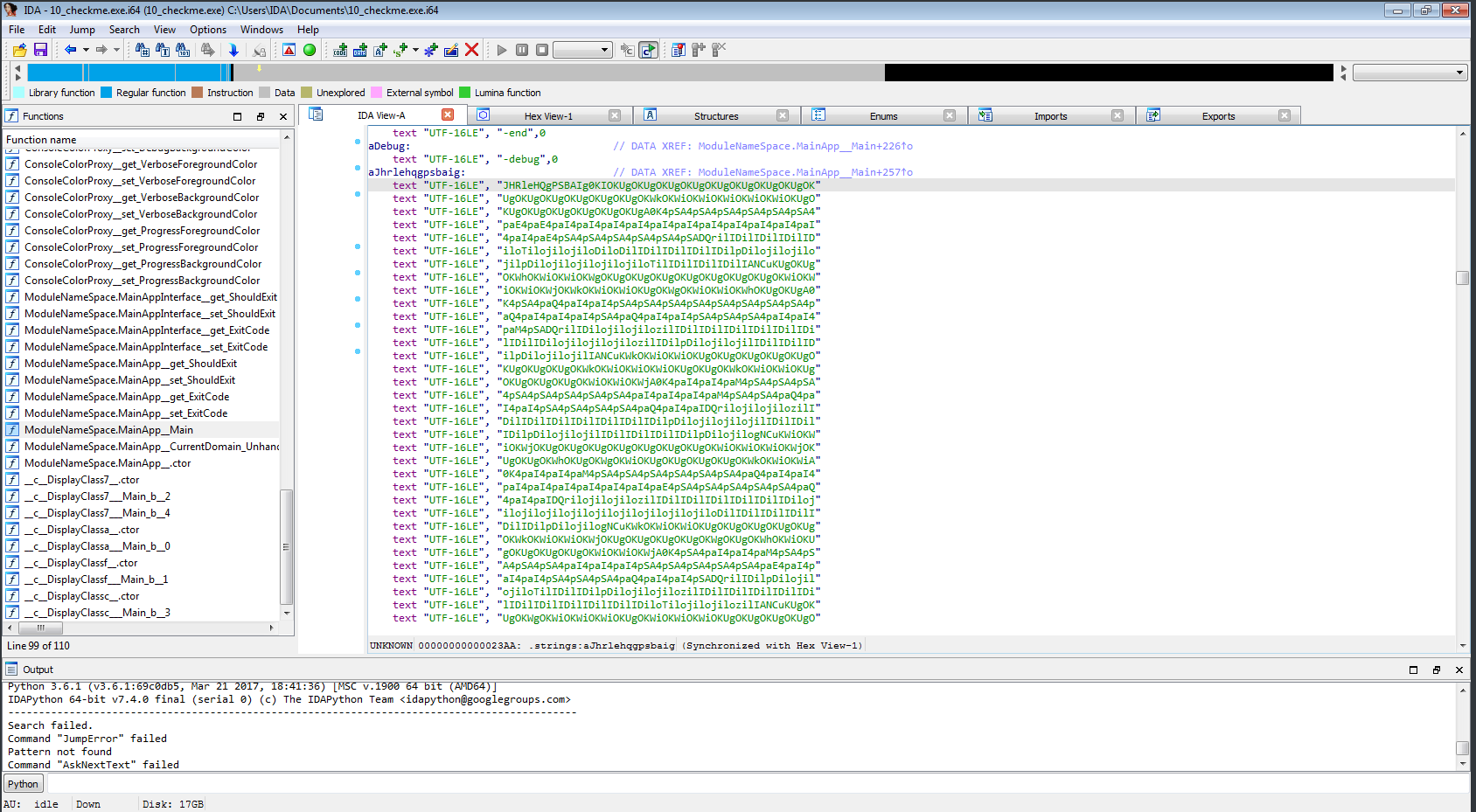
And decode it in CyberChef: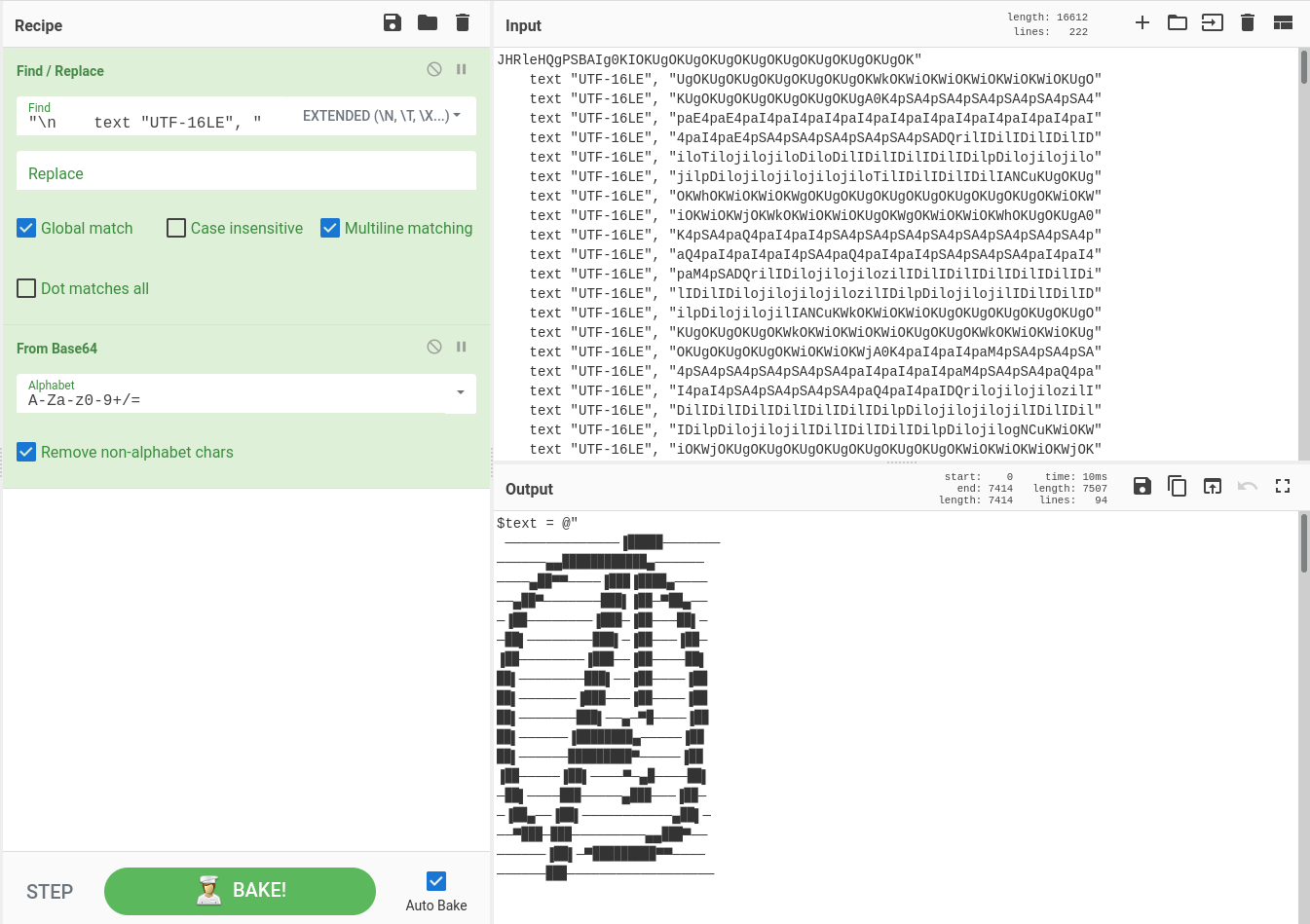
And here we go! A powershell script!
$text = @"
──────────────▐█████───────
──────▄▄████████████▄──────
────▄██▀▀────▐███▐████▄────
──▄██▀───────███▌▐██─▀██▄──
─▐██────────▐███─▐██───██▌─
─██▌────────███▌─▐██───▐██─
▐██────────▐███──▐██────██▌
██▌────────███▌──▐██────▐██
██▌───────▐███───▐██────▐██
██▌───────███▌──▄─▀█────▐██
██▌──────▐████████▄─────▐██
██▌──────█████████▀─────▐██
▐██─────▐██▌────▀─▄█────██▌
─██▌────███─────▄███───▐██─
─▐██▄──▐██▌───────────▄██▌─
──▀███─███─────────▄▄███▀──
──────▐██▌─▀█████████▀▀────
──────███──────────────────
Get into the Thanos's secret vault and save the world or just get the flag.. :) `n
"@;
Write-host $text; $main = ("{2}{0}{1}{3}"-f'df','gIFSsslf','fdg','flag');
#import socket;
def netcat(hostname, port, content):;s = socket.socket(socket.AF_INET, socket.SOCK_STREAM);s.connect((hostname, port));s.sendall(content);s.shutdown(socket.SHUT_WR);while 1:;data = s.recv(1024);if data == "":;break; print "Received:", repr(data);print "Connection closed.";s.close()
$name = Read-Host ("{0}{1}"-f 'Logi','n');
$pass = Read-Host ("{0}{2}{1}"-f'P','ssword','a');
Write-Host "`n";
$spacestone = ("{1}{2}{0}"-f 'lz','SW5','maW5pdH');
$mindtone = ("{1}{0}{2}" -f'D','sdaoISA','Ads');
$realitystone = ("{2}{1}{0}"-f 'Sosa=','WEVL','Is');
$powerstone = ("{2}{0}{1}" -f'W','NASO','nvio');
$soulstone = ("{2}{1}{0}" -f'Q=','DBuMy','d');
$timestone = ("{1}{0}" -f 'FDek','ugfU');
if (([System.Convert]::ToBase64String([System.Text.Encoding]::UTF8.GetBytes($name.ToLower())) -eq ("{1}{0}{2}"-f'Gh','d','hbm9z')) -and ([System.Convert]::ToBase64String([System.Text.Encoding]::UTF8.GetBytes($pass)) -eq (-join($spacestone, $soulstone)))) {$sanctuary = ("{2}{3}{8}{10}{12}{1}{9}{7}{4}{5}{6}{11}{0}"-f'gMzMgNzIgN2Q=','g','NDYgN','GMgNDE','gNDA','gN','z','gNzIgNGQ','gND','NjIgMzM','cgN2IgN','MgNzQ','DMgNzk');[System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String($sanctuary)).Split(" ") | forEach {[char]([convert]::toint16($_,16))} | forEach {$out = $out + $_};Write-Host ('Gre'+'a'+'t '+'job!'+' '+'H'+'ere '+'is'+' '+'your'+' '+'rewa'+'rd:'+' '+' '+"`n");Write-host ("{2}{1}{4}{3}{0}"-f '=','==','=','=========','====');Write-host $out;Write-host ("{2}{1}{3}{0}"-f '===','===','========','===');} else {Write-Host ((("{2}{0}{1}{3}"-f'e tr','y!','Nic',' :)')));};
$commands = @"
Add-content This cmdlet adds the content to the specified file.
Add-Computer This cmdlet adds the local computer to a domain or workgroup.
Add-History This cmdlet is used to add the command in the history.
Add-jobTrigger This cmdlet adds the job triggers to the scheduled jobs.
Add-member The cmdlet adds the custom methods or properties to an instance of a PowerShell object.
Add-type This cmdlet adds a Microsoft .NET framework class to a Windows PowerShell session.
Clear-Content This cmdlet deletes the content of a file, but not delete that file.
Clear-History This cmdlet deletes the entries from the command history.
Clear-Item This cmdlet clears the value of item or variable, but not clear that item or a variable.
Clear-ItemProperty This cmdlet clears the value of a property but not delete that property.
Clear-Variable This cmdlet deletes the value of a variable.
Clear-Host This cmdlet clears the display of the host program.
Copy-ItemProperty This cmdlet copies a value and property from a specified location to another location.
Copy-Item This cmdlet copies an item from one location to another.
Complete-Transaction This cmdlet commits the active transaction.
Compare-object This cmdlet compares two sets of objects.
Disable-PSBreakpoint This Cmdlet disables the breakpoint in the current console.
Enable-PSBreakpoint This Cmdlet enables the breakpoint in the current console.
Find-package This cmdlet finds the software packages in the available packages sources.
Find-script This cmdlet is used to find a script
ForEach-Object This cmdlet performs an operation on each item in a collection of input objects.
Get-Alias This cmdlet gets the aliases for the current session.
Get-childItem This cmdlet gets the item and the child items in one or more specified locations.
Get-Command This cmdlet is used to get all commands.
Get-Content This cmdlet gets the content of the file at the specified location.
Get-Date This cmdlet is used to get the current date and time.
Get-ExecutionPolicy This cmdlet gets the execution policy for the current session.
Get-Help This cmdlet displays information about PowerShell commands and concepts.
Get-History This cmdlet displays a list of commands which are entered during the current session.
Get-host This cmdlet gets an object which represents the current host program.
Get-InstalledScript This cmdlet gets a script which is installed for the current user.
Get-Item This cmdlet gets the item or a file at a particular location.
Get-ItemProperty This cmdlet gets the properties of a particular item.
Get-Location This cmdlet displays the current working location.
Get-PSBreakpoint This cmdlet gets the breakpoint which is set in the current session.
Get-Package This cmdlet displays the list of all installed packages by using the package management.
Get-Process This cmdlet gets the processes which are running on local or remote computers.
Get-Service This cmdlet gets the services on local or remote computers.
Get-Transaction This cmdlet gets the currently active transaction.
Get-Variable This cmdlet gets the variable in the current console.
Install-package This cmdlet is used to install one or more software packages.
Install-script This cmdlet is used to install a script.
Invoke-commands This cmdlet executes commands on local and remote computers.
Move-Item This cmdlet is used to move an item from one location to another.
Move-ItemProperty This cmdlet is used to move the property of an item from one location to another.
New-alias This cmdlet creates a new alias.
New-Item This cmdlet creates a new item.
New-ItemProperty This cmdlet creates a new property for an item and sets its value.
New-Service This cmdlet creates a new Window service.
New-variable This cmdlet creates a new variable.
Read-Host This cmdlet reads a line of inputs from the console.
Remove-computer This cmdlet removes a local computer from its domain.
Remove-Item This cmdlet deletes the particular item.
Remove-ItemProperty This cmdlet deletes the property & its value from an item.
Remove-job This cmdlet removes the background job of Windows PowerShell.
Remove-PSBreakpoint This cmdlet deletes the breakpoint from the current console.
Remove-variable This cmdlet deletes a variable with its value.
Rename-computer This cmdlet is used to rename a computer.
Restart-Service This cmdlet stops and starts one or more services.
Restart-computer This cmdlet is used to restart the Windows operating system on local and remote computers.
Resume-job This cmdlet is used to restart a suspended job.
Save-Help It is used to download and save the newest help files to a file system directory.
Save-packages This cmdlet is used to save the packages to the local computer without installing them.
Save-Script This cmdlet is used to save a script.
Select-string This cmdlet is used to find the text in string or files.
Send-MailMessage This cmdlet is used to send an e-mail message.
Set-Alias This cmdlet creates or changes the alias for a cmdlet in the current Windows PowerShell.
Set-content This cmdlet writes the content in a file.
Set-Date This cmdlet changes the time of the system.
"@
After reverse engineering the script and concating some strings we recover the correct login credentials as well as the flag.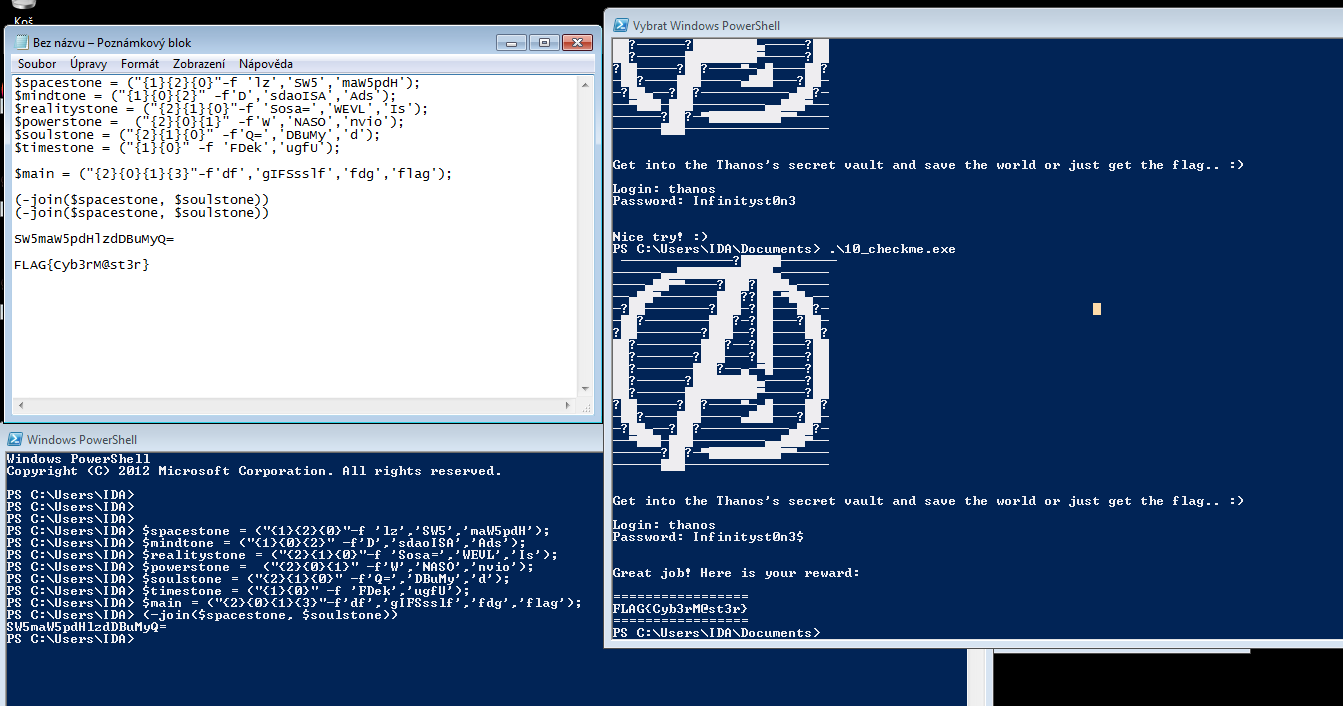
Flag: FLAG{Cyb3rM@st3r}
Zranitelnost
We are provided with a piece PHP source code and are supposed to identify the vulnerability in it.
<?php
if (!file_exists('log.on')) {
echo "Logs are disabled by default.";
exit;
}
$uuid = $_GET["filter"];
$storedLogs = "/tmp/stored-logs/{$uuid}";
if (file_exists($storedLogs)) {
header('Content-Type: application/json');
header("Access-Control-Allow-Origin: http://localhost:3000");
echo file_get_contents($storedLogs);
} else {
echo "log file does not exist";
}
?>
If logging is enabled, we can path traverse using the filter parameter and the page will return whichever file we want.
Flag: path traversal - LFI
Red Team
In the .zip provided there are SAM, SOFTWARE etc. Windows registry files AKA hives. We are supposed to find from which system version they come from, what was the installation time, what is the hash of the password of local admin and what is his password (knowing it is 4 characters long).
The answers to the first two questions can be found in the SOFTWARE hive in SOFTWARE\Microsoft\Windows NT\CurrentVersion, we just need to convert InstallDate from hex to decimal and convert the resulting unix time stamp. I’m on Linux, so I use the hivexsh utility.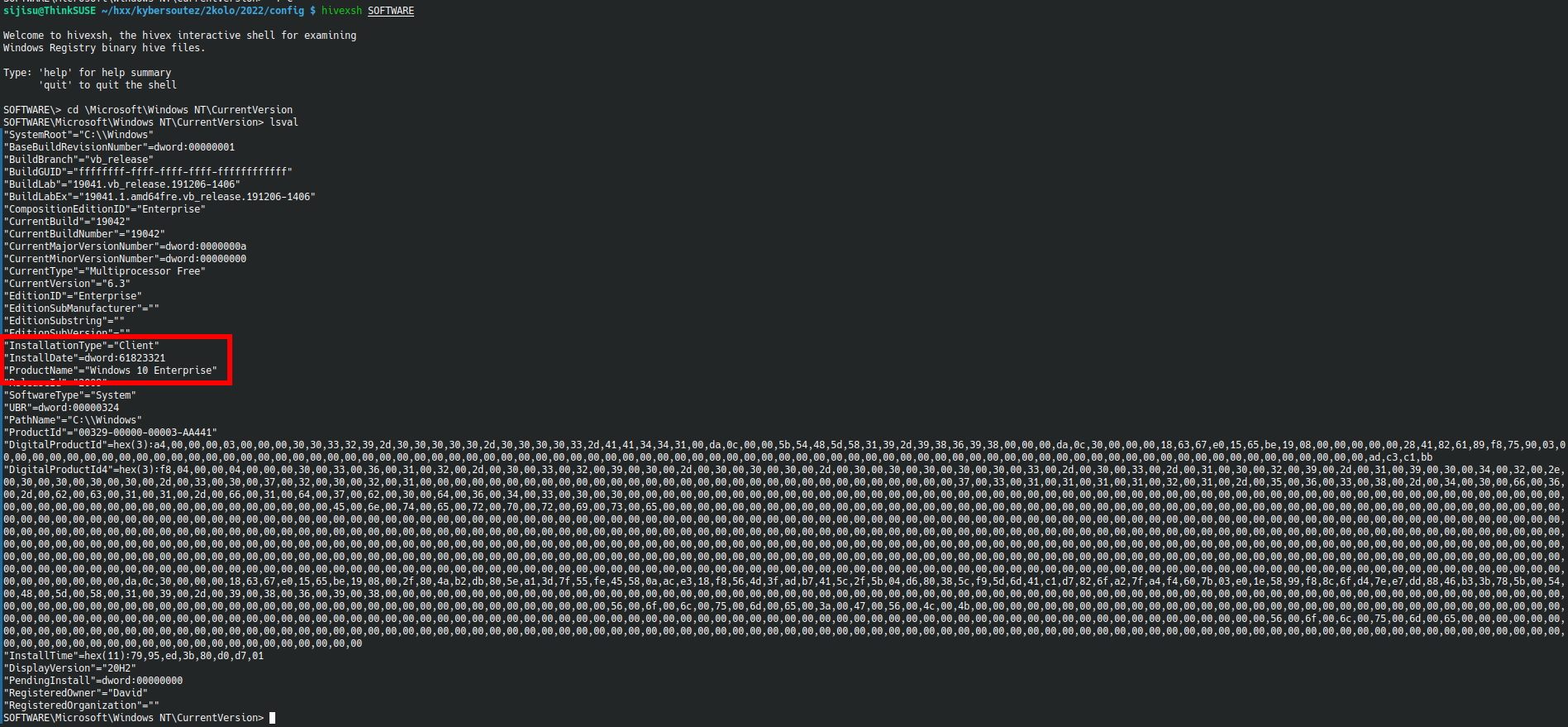
For the other two, we have to use mimikatz and the SAM and SYSTEM hives. We use mimikatz like: lsadump::sam /system:C\Pathto /sam:C:\Pathto The first user, with RID 500 is local admin - David.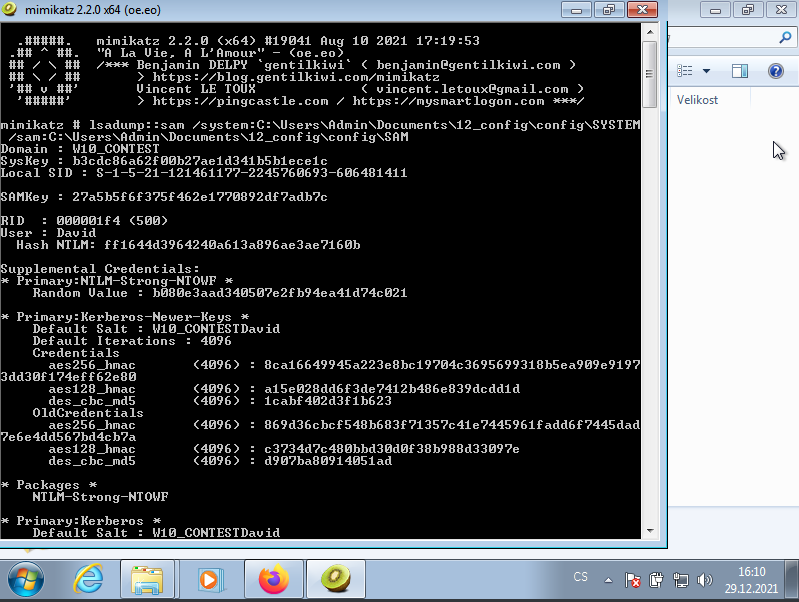
We then take his NTML hash and feed it to john. Like: john --format=NT --incremental --length=4 hash.txt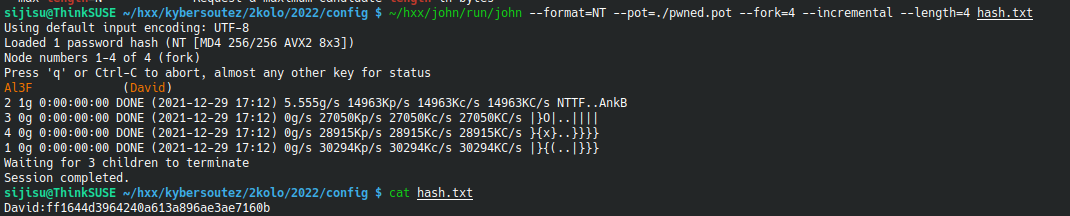
Flag 1: Windows 10 Enterprise
Flag 2: 03.11.2021 07:58:41 (UTC+1)
Flag 3: ff1644d3964240a613a896ae3ae7160b
Flag 4: Al3F
Díra na webu
This is a blackbox web challenge. We are given an URL http://ks2021.ncko.cz/, where we find a login page.
I got stuck for a while here. I tried the classics: SQL Injection, Parameter Injection, LDAP Injection… But nothing worked.
Then my dirbusting finished and it found something extra peculiar: /README.md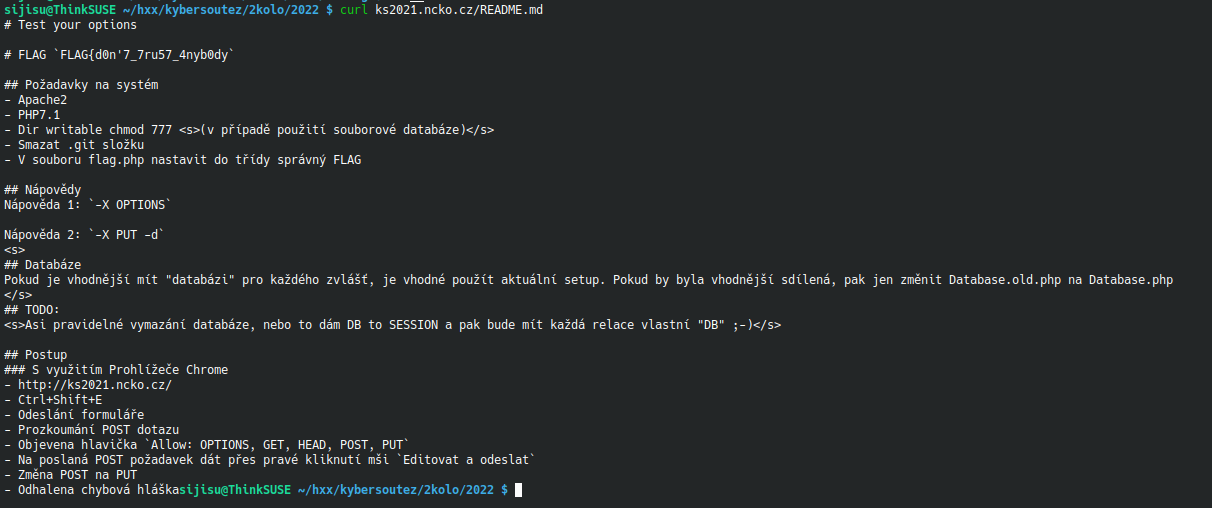
The website was deployed with a README.md containing all the deployment instructions, solution and the flag publicly visible. The person who wrote the deployment instructions in the README forgot to mention that they should remove the README file itself lol.
So now that we know how to solve the challenge let’s do exactly that. We register ourselves an account using the PUT method.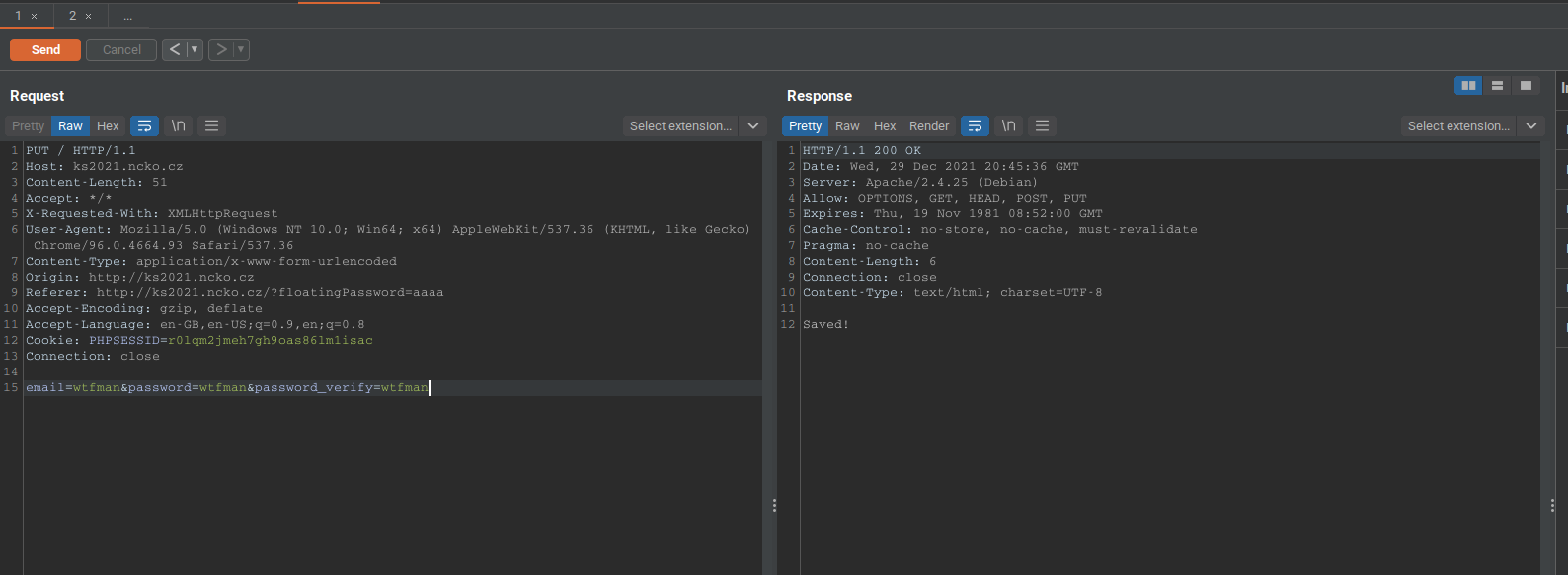
Now if we try to login a flag is printed.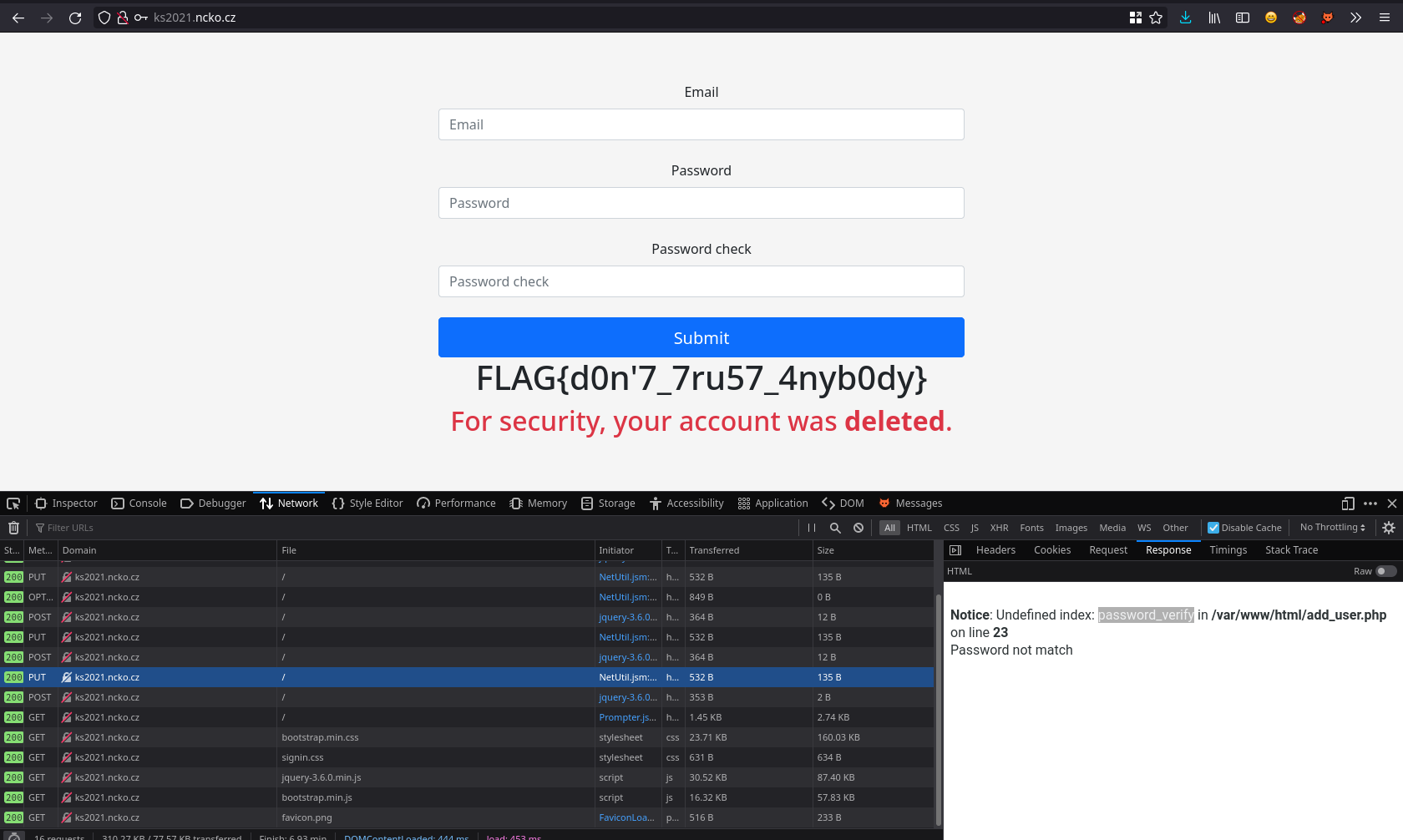
Flag: FLAG{d0n'7_7ru57_4nyb0dy}
Reverse Proxy
Another (almost) blackbox web challenge. URL: https://www.sskb-ey21.tech We are presented with a blog about CS:
In the last blog post there is not only a link to a very helpful article, but also a hint pointing to nginx vulnerabilities. This is going to be about bypassing reverse proxies.
After initial dirbusting we find /robots.txt and in it links to nginx config files of the server, knowing what’s in them can speed up the exploitation.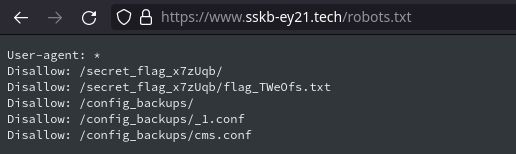
Now back to the article, in Example 2 it is shown, how nginx with the following config:
location /to_app {
proxy_pass http://server/any_path/;
}
Will when we request /to_app../other_path forward http://server/any_path/../other_path. Because as it turns out the server behind the nginx is Apache, that normalizes /any_path/../other_path to /other_path, we can escape the /any_path/ restriction and access any files we want behind the reverse proxy.
We can quickly check and see this exact config pattern in the cms.conf file.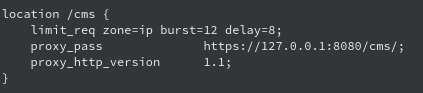
We can verify the vulnerability by checking a non existent URL with curl. And indeed we get a different 404 than the CMS one, that means we traversed the path up.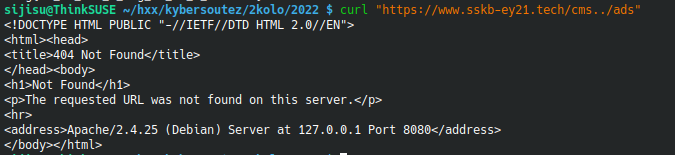
Here I got stuck, not knowing where I was supposed get the flag. I figured I can access Apache’s /server-status, but noone was accessing the server except me. Then I remembered the weird flag paths from /robots.txt file and tried that. Indeed I found the flag in https://www.sskb-ey21.tech/cms../secret_flag_x7zUqb/flag_TWeOfs.txt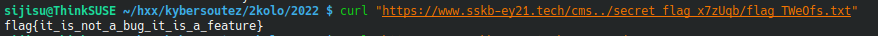
Flag: flag{it_is_not_a_bug_it_is_a_feature}
Triviální zranitelnost
Another PHP code snippet and task to find a vulnerability.
<?php
echo "<h1>Company backoffice portal</h1>";
$name = $_GET['name'];
echo "<p>Welcome user <b>$name</b></p>";
echo "<p>Here is your main menu:</p>";
echo "<li><a href=\"https://www.flowmon.com\">Download your payroll</a></li>";
echo "<li><a href=\"https://www.flowmon.com\">Ask for vacation</a></li>";
echo "<li><a href=\"https://www.flowmon.com\">Book a business trip</a></li>";
?>
This is obviously an XSS vulnerability in the name parameter.
Flag: XSS
URL transformace
We are given an URL we should transform step by step to get the flag.
I solved this using this CyberChef recipe
Accessing the result https://www.cybersecurity.cz/cybersecurityr/pwge.html gives the flag.
Flag: JSEMKYBER
UUENCODE
We get this encoded text we are expected to decode and enter the last three words of the plaintext.
M3<.A;2!P;\2-PZUT8<2-(&$@=FER='7#H6QNPZT@:FW#J6YO+B!:;L.A;2!)
M;G-T86=R86TL(%=H871S87 @82!6:6)E<BX@5GET=F_%F6EL(&IS96T@<VEL
F;L.I('1A:F[#J2!H97-L;RX@2G-E;2!396-U<FET>2!#>6)E<B
We google “UUENCODE online”, find this online convertor.
Decoded:
Mám počítač a virtuální jméno. Znám Instagram, Whatsap a Viber. Vytvořil jsem silné tajné heslo. Jsem Security Cyber
Flag: Jsem Security Cyber
ROT8000
We get this encoded text we are expected to decode and do enter what we are told in the result.
籛籘籝籁簹簹簹 籹絀籮籿糈籭糔 籛籘籝簺簼 籭籸 籶籸籭籮类籷糔籱籸 籭籲籰籲籽糈籵籷糔籱籸 籹类籸籼籽絀籮籭糔簷 籙籸籴籾籭 籷籮粃籷糈籽籮 糴糔籷籼籴糐 粃籷籪籴粂簵 籹籪籴 籷籮籷糔 籱籷籮籭 粃絀籮米籶糐簵 絥籮 米籭籮 籸 米籮米籲籬籱 籿粂籾絥籲籽糔 籿 籽籸籶籽籸 籼粂籼籽糐籶籾 鯮 籽米簷 籹籸籼籾籷 粃籷籪籴絖 籶籮粃籲籷糈类籸籭籷糔 籪籫籮籬籮籭粂 籸 籁簹簹簹 籹籸粃籲籬簷 籓籪籴籸 籭絖籴籪粃 籿粂絀籮絈籮籷糔 籽糐籽籸 糡籵籸籱粂 粃籪籭籮米籽籮籃 籛籘籝籁簹簹簹
We google “ROT8000 online”, find this online convertor.
Decoded:
ROT8000 převádí ROT13 do moderního digitálního prostředí. Pokud neznáte čínské znaky, pak není hned zřejmé, že jde o jejich využití v tomto systému – tj. posun znaků mezinárodní abecedy o 8000 pozic. Jako důkaz vyřešení této úlohy zadejte: ROT8000
Flag: ROT8000
IoT systém
The .tar.gz included is a linux file system that was “infected with something that is causing a high CPU load” and we are supposed to find out the name of the executable the attacker installed and ran.
In /home/admin we can find binary called minerd a well-known crypto miner and nohup.out file with evidence it ran.
Flag: minerd
Statická síťová analýza
We are provided a PCAP in which are we supposed to find all username+password pairs and count them.
We do it manually + let some filters help us, for example:
Get all tcp stream IDs: tshark -r AFCEA-FTP+HTTP.pcapng -T fields -e tcp.stream ftp | sort -n -u
Show one stream: tshark -r AFCEA-FTP+HTTP.pcapng -qz follow,tcp,ascii,15 ftp
Filter for http POST requests: http.request.method==POST
Flag: 6
NOTE: It turned out there were only 5 unique username+password pairs, but they accepted 6 as well as 5, as it was not clear from the description if to count duplicates.
ADS - Capture the Flag
As the name suggest, this is a challenge about NTFS ADS. We are given a .wim file.
The intended solution would probably be to mount the .wim somehow and extract the flag from ADS. But since I’m a Linux person and the image was small (~500KiB) I opened the file in hex editor, copied the first thing from the end that looked like base64, decoded it and it was the flag indeed.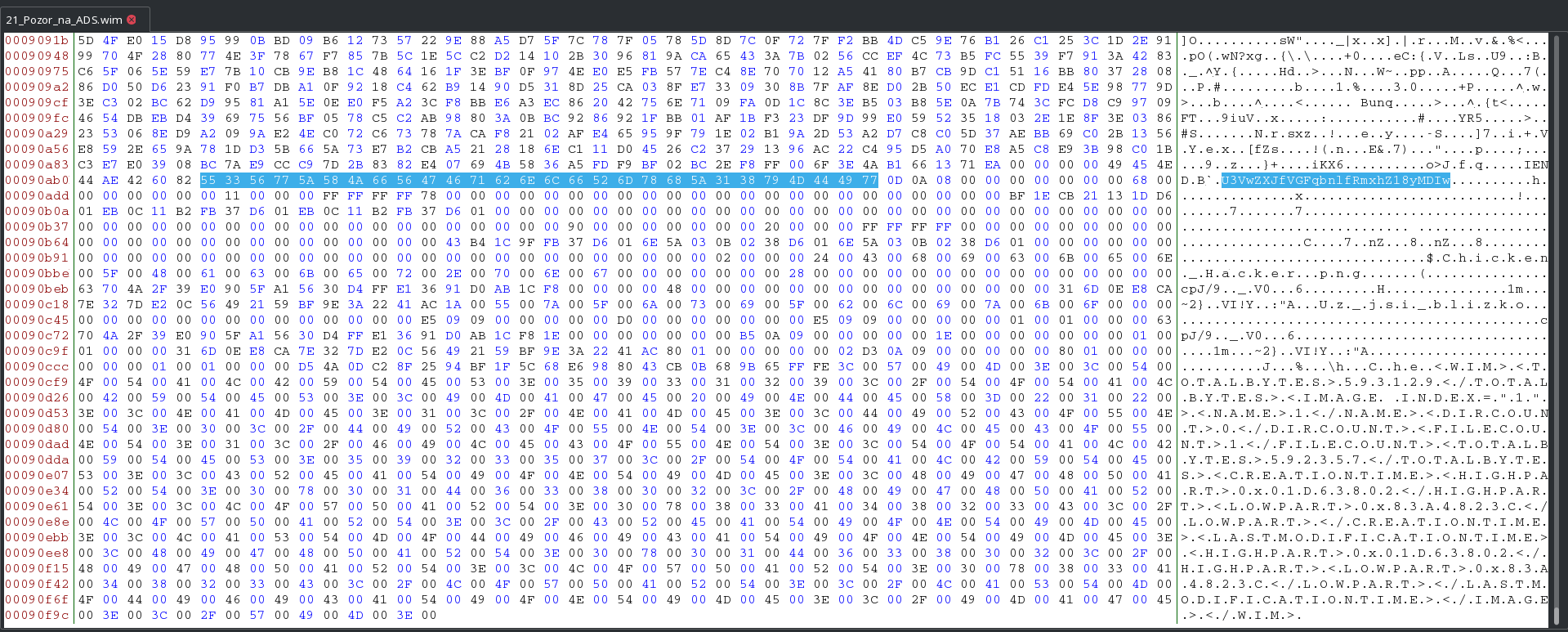
Flag: Super_Tajny_Flag_2020
Frekvenční analýza
Another substitution cipher challenge this time in English. We are supposed to enter the first and the last word of the plaintext. Ciphertext is the following:
PCQ VMJYPD LBYK LYSO KBXBJXWXV BXV ZCJPO EYPD KBXBJYUXJ LBJOO KCPK. CP LBO LBCMKXPV XPV IYJKL PYDBL.
QBOP KBO BXV OPVOV LBO LXRO CI SX'XJMI, KBO JCKO XPV EYKKOV LBO DJCMPV ZOICJO BYS, KXUYPD:
"DJOXL EYPD, ICJ X LBCMKXPV XPV CPO PYDBLK Y BXNO ZOOP JOACMPLYPD LC UCM LBO IXZROK CI FXKL XDOK XPV
LBO RODOPVK CI XPAYOPL EYPDK. SXU Y SXEO KC ZCRV XK LC AJXNO X IXNCMJ CI UCMJ SXGOKLU?"
OFYRCDMO, LXROK IJCS LBO LBCMKXPV XPV CPO PYDBLK
We use this substitution solver to crack the key.
NOW DURING THIS TIME SHAHRAJAD HAD BORNE KING SHAHRIYAR THREE SONS. ON THE THOUSAND AND FIRST NIGHT.
WHEN SHE HAD ENDED THE TALE OF MA'ARUF, SHE ROSE AND KISSED THE GROUND BEFORE HIM, SAYING:
"GREAT KING, FOR A THOUSAND AND ONE NIGHTS I HAVE BEEN RECOUNTING TO YOU THE FABLES OF PAST AGES AND
THE LEGENDS OF ANCIENT KINGS. MAY I MAKE SO BOLD AS TO CRAVE A FAVOUR OF YOUR MAXESTY?"
EPILOGUE, TALES FROM THE THOUSAND AND ONE NIGHTS
Flag: NOW NIGHTS
Something Weird
We are given a password-protected .zip archive. That’s it.
After a moment I noticed the archive name 23_7d720b89f62acec63ff581c37e96c8b5.zip was kinda sus. I decided to feed the hash to CrackStation and indeed the string 7d720b89f62acec63ff581c37e96c8b5 is a MD5 hash of MichaelJackson.
When we try that as a password, we successfully unzip the archive and then find the flag in an exif property of the image.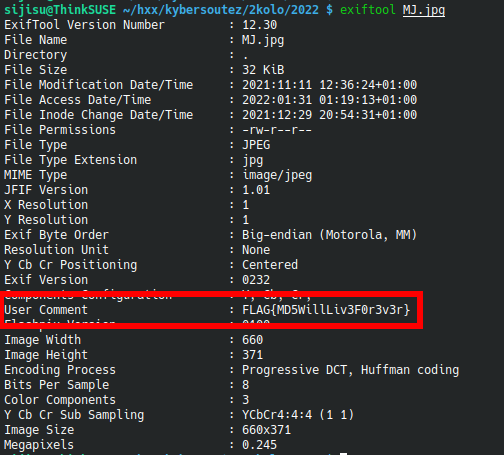
Flag: FLAG{MD5WillLiv3F0r3v3r}
Vernamova šifra
Vernam cipher it is, ladies and gentlemen. We are given an encrypted message.
150d0 31f10 41054 51509 03491 94555 044a0 30447 03030 04d5d 13101 00619
And are told that some portion of the following Lorem ipsum text was used as the password.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Quisque hendrerit lorem vel nibh dignissim
eleifend. Fusce non dignissim ligula, a suscipit felis. Nam congue congue neque, malesuada efficitur
massa viverra sed. Nullam id justo ut quam rhoncus elementum sed vitae metus. Cras finibus blandit
hendrerit. Fusce et sapien dui. Praesent vulputate lacinia pulvinar. Nunc tincidunt placerat leo non
sodales. Vivamus pretium, dui vitae dictum luctus, dolor risus placerat leo, nec consequat lorem nisl
eu nulla. Mauris aliquam felis ut turpis dictum, eget sodales diam luctus. Fusce lorem magna, egestas
in nunc eu, eleifend finibus odio. Sed arcu sapien, gravida vitae leo eu, facilisis euismod metus.
Donec mi magna, tristique sed nisl et, lacinia placerat nibh. Quisque sollicitudin sapien nisi,
quis accumsan eros feugiat in. Sed facilisis eros sed odio consequat, ut ultricies sem iaculis.
If you don’t know Vernam cipher is basically XOR OTP. So I came up with this simple python script that will bruteforce all the possible offsets of the key in Lorem ipsum:
import sys
def xor(shorter, longer, index):
result = b''
for i, item in enumerate(shorter):
##print(item, longer[index:][i])
result += bytes([item ^ int.from_bytes(longer[index:][i].encode(), sys.byteorder)])
return result
ciphertext = bytearray.fromhex("150d0 31f10 41054 51509 03491 94555 044a0 30447 03030 04d5d 13101 00619".replace(" ", ""))
key = """Lorem ipsum dolor sit amet, consectetur adipiscing elit. Quisque hendrerit lorem vel nibh dignissim
eleifend. Fusce non dignissim ligula, a suscipit felis. Nam congue congue neque, malesuada efficitur
massa viverra sed. Nullam id justo ut quam rhoncus elementum sed vitae metus. Cras finibus blandit
hendrerit. Fusce et sapien dui. Praesent vulputate lacinia pulvinar. Nunc tincidunt placerat leo non
sodales. Vivamus pretium, dui vitae dictum luctus, dolor risus placerat leo, nec consequat lorem nisl
eu nulla. Mauris aliquam felis ut turpis dictum, eget sodales diam luctus. Fusce lorem magna, egestas
in nunc eu, eleifend finibus odio. Sed arcu sapien, gravida vitae leo eu, facilisis euismod metus.
Donec mi magna, tristique sed nisl et, lacinia placerat nibh. Quisque sollicitudin sapien nisi,
quis accumsan eros feugiat in. Sed facilisis eros sed odio consequat, ut ultricies sem iaculis."""#.replace("\n", "").replace(" ", "")
for i in range(0, len(key)-len(ciphertext)):
candidate = xor(ciphertext, key, i)
print(candidate)
That will print out a lot of candidates, but we luckely have a nudge from the description, that we are looking for a “password” or “heslo” in Czech. So let’s try to look for that: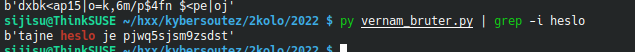
Success!
Flag: pjwq5sjsm9zsdst
Analýza alertu
You get an alert from the Fidelis platform and are supposed to tell something about it: if it was a communication with a honeypot and some other stuff concerning nmap Idle Scans.
Flag 1: b. Komunikací se síťovou pastí
Flag 2: d. Klient vystavujíc spojení byl v internetu a server v interní síti
Flag 3: c. Může se jednat o výsledek skenování pomocí Idle Scan techniky
Flag 4: a. Nález potvrzuje, že si málokdo pamatuje všechny parametry nástroje nmap
NOTE: This last answer is very controversial, all the people I talked to had different answers.
Published on
